WordPress Hacks: The Japanese Keyword Hack (and how to fix it)
Is your website suddenly showing tens of thousands of pages with Japanese language, like this?
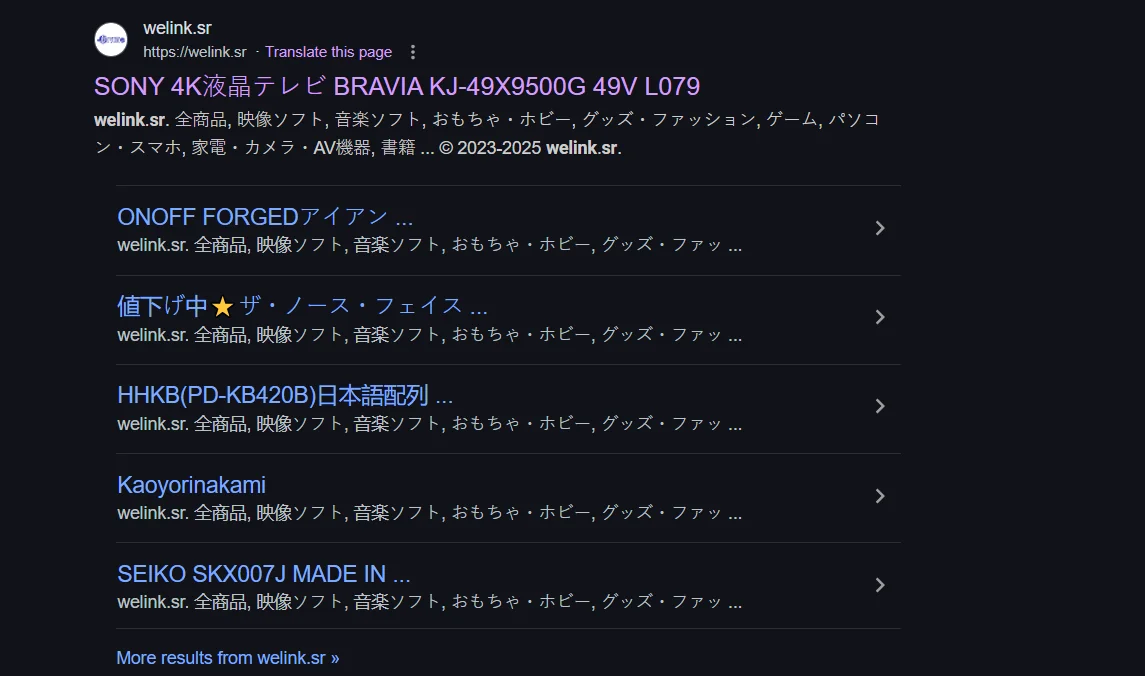
Image from Reddit
Here’s the bad news: you’ve been effected by the Japanese Keyword Hack.
But good news: here’s a guide to fix it.
What is the Japanese Keyword Hack?
The Japanese Keyword Hack, also known as Japanese SEO spam, is a malicious tactic where attackers infiltrate your website to create numerous pages filled with Japanese text and links to fraudulent sites.
These pages are designed to manipulate search engine rankings, often leading to a significant drop in your site’s SEO performance and credibility.
In some cases, hackers may even add themselves as property owners in your Google Search Console to further exploit your site’s settings.
How to Identify if Your Site is Affected
- Google Search Check: Perform a search using
site:yourdomain.com. If you notice pages with Japanese characters or unfamiliar URLs, it’s a strong indication of the hack. - Google Search Console Alerts: Check for any security warnings or notifications about spam content.
- Unusual Site Behavior: Look for unexpected redirects, unfamiliar user accounts, or a sudden increase in indexed pages.
Are Certain Plugins Responsible for This?
Yes, some plugins—especially outdated or poorly maintained ones—are frequent targets and vectors for these types of attacks. Below are the most commonly exploited plugin categories that can lead to the Japanese Keyword Hack.
1. Abandoned Plugins
Plugins that haven’t received updates in over a year may contain unpatched vulnerabilities. Hackers actively scan for these. If you’re using any plugin that hasn’t been updated recently or shows a warning in the WordPress admin, consider replacing it with a well-maintained alternative.
2. File Upload Plugins
Plugins that allow users to upload files (contact forms, frontend file managers, etc.) can be dangerous if not coded securely. Improper file validation opens the door to uploading malicious PHP scripts.
Risky examples include:
- Older versions of Contact Form 7 or WPForms
- Plugins like File Manager or Advanced File Manager
3. SEO and Redirection Plugins
Some SEO tools and redirection plugins have been abused to inject cloaked spam or redirect Googlebot to malicious pages while showing something normal to users.
Watch out for: Misconfigured or outdated All in One SEO Pack, Rank Math, or sketchy redirection plugins.
4. Page Builder Plugins
Page builders that render shortcodes dynamically can be manipulated to load hidden content. If a plugin allows frontend content creation or editing, it should be heavily locked down.
Risk-prone examples:
- Older versions of Elementor
- WPBakery with third-party extensions
- Outdated SiteOrigin Page Builder installs
5. Pirated Themes or Plugins
If you’ve ever installed a “nulled” or pirated plugin or theme, it may contain a hidden backdoor or malware that activates later. These often inject base64-encoded PHP in files like functions.php or into random plugin folders.
How to Check If a Plugin Is Responsible
- Use a malware scanner like Wordfence or Sucuri to detect infected files.
- Check the file modification dates in
/wp-content/plugins/for recent unexpected changes. - Look at your access logs for strange POST requests or plugin-based paths being hit.
Steps to Fix the Japanese Keyword Hack
1. Backup Your Website
Before making any changes, ensure you have a complete backup of your website, including files and databases. This precaution allows you to restore your site if needed.
2. Remove Unauthorized Users from Google Search Console
Access your Google Search Console and navigate to the “Users and Permissions” section. Remove any unfamiliar users to prevent further unauthorized access.
3. Scan and Clean Your Website
- Use Security Plugins: Employ reputable security plugins like Wordfence or Sucuri to scan your website for malware and malicious code.
- Manual Inspection: Review your site’s files, especially
.htaccess,wp-config.php, and theme files, for any suspicious code or unfamiliar entries. - Database Check: Examine your database for unauthorized entries, particularly in the posts and options tables.
4. Remove Malicious Content
Delete any pages, posts, or files that were added without your knowledge. Ensure that your sitemap is clean and doesn’t contain any of the spammy URLs.
5. Request Removal of Hacked Pages from Google’s Index
- Manual Removal: Use the “Remove URLs” tool in Google Search Console to request the removal of specific URLs.
- Bulk Removal: For a large number of URLs, consider using the “Remove Outdated Content” tool or third-party extensions that facilitate bulk URL submissions.
6. Update and Secure Your Website
- Update Software: Ensure that your CMS, themes, and plugins are up to date to patch any security vulnerabilities.
- Change Passwords: Update all passwords associated with your website, including admin, FTP, and database credentials.
- Implement Security Measures: Install security plugins, set up firewalls, and consider enabling two-factor authentication to enhance your site’s security.
7. Double Check There Are No Sitemaps Lingering
- Often when this attack occurs, they root these pages in your sitemap directly, or other sitemaps.
- Scan to verify you’ve truly eliminated all sitemaps related to these pages. Even if these are now 404 pages, you want to pluck this weed.
How Long Will It Take for Google to Remove and Re-index?
The age-old question. It’s critical to do all of the above to clean up as fast as possible.
From that point on, it’s up to Google when these results reset. It moves at its own pace, so be sure your fixes stick, and then hurry up and wait.
How to Prevent Future Attacks
- Regular Monitoring: Periodically check your site’s indexed pages using
site:yourdomain.comto detect any anomalies early. - Limit Plugin Use: Only use essential and well-maintained plugins to reduce potential vulnerabilities.
- Disable Directory Browsing: Prevent unauthorized access to your site’s directories by disabling directory browsing.
- Set Proper File Permissions: Ensure that your files and directories have appropriate permissions to prevent unauthorized modifications.
- Regular Backups: Maintain regular backups of your website to facilitate quick recovery in case of future issues.
- Consider Static WordPress: the most secure WordPress in the game.
How the Headless Hostman Can Help
The Headless Hostman takes your WordPress site — as-is — and converts it to a Static Version.
This means the Live website is completely decoupled from the database and all of the endpoint that might be typically exposed to these vulnerabilities.
Beyond that, we offer multiple ways to further lockdown your WordPress website including:
- The ability to “put your WordPress website to sleep” while the live site stays up
- Two-step login authentication. Basically, anyone without portal access is blocked immediately
Looking for peace of mind for your site? Switching to Static WordPress is your best bet.
Deeper into the Abyss