How Hackers Really Mine WordPress Admin Email Addresses (And How to Outsmart Them)
WordPress powers more than 40% of the internet, and with that dominance comes a target on its back. Most site owners understand the basics of WordPress security—keep plugins updated, use strong passwords, avoid “admin” as your username. But what about your email address?
Here’s the reality: if your admin email is exposed, you’re already halfway compromised. And if that email has been associated with password data-leaks, you’re well on your way to getting hacked.
Email is the skeleton key in countless attack strategies: brute-force logins, password resets, phishing campaigns, social engineering attacks, even domain hijacking. And yet, many WordPress sites unknowingly hand it over.

The Obvious Ones (Still Worth Mentioning)
Before we get into the darker corners, let’s quickly revisit the basics—because even in 2025, most hacked WordPress sites fell for the easy stuff:
1. Author Archives
Most WordPress installs generate public author pages at URLs like:
example.com/author/admin/
Depending on your theme and plugins, these pages can expose not just usernames but sometimes bios, profile fields, and yes, even email addresses.
Prevent it:
- Use a plugin like Rank Math to
noindexor disable author archives. - Obfuscate author slugs using the Edit Author Slug plugin.
- Don’t use your admin account to publish posts—create a “writer” role with no backend access.
2. REST API Enumeration
The WP REST API is powerful — but unguarded, it leaks:
/wp-json/wp/v2/users
Unless restricted, this endpoint exposes usernames, slugs, and sometimes custom meta. That metadata can include email addresses (especially when plugins or themes don’t sanitize fields properly).
Prevent it:
add_filter('rest_endpoints', function( $endpoints ) {
unset( $endpoints['/wp/v2/users'] );
return $endpoints;
});Or selectively block user access with conditional logic based on authentication or roles.
Be cautious doing this without prior research. You may have a Plugin or two that relies on this that may require access. In that case, investigate authorizing them.
Now Let’s Go Deeper: Advanced Mining Techniques
Here’s where the average security post stops—but the average hacker doesn’t.
Below are lesser-known or more sophisticated methods used to mine WordPress admin emails, particularly in targeted or large-scale automated attacks.
3. Correlating Gravatar Hashes to Public Profiles
If you use Gravatar, your email is hashed into an MD5 string and embedded in the page:
<img src="https://www.gravatar.com/avatar/92eb5ffee6ae2fec3ad71c777531578f?s=96">A hacker can reverse this MD5 using databases like Hashes.org or correlate it to a known Gravatar profile—confirming the admin’s identity and email pattern.
It’s really easy, too. Grok or ChatGPT can crack an MD5 in a couple of seconds.
Prevent it:
- Use a non-public email for admin roles.
- Disable Gravatar under Settings > Discussion.
- Use a plugin like Disable User Gravatar.
4. Comment System Metadata Scraping
Comment systems can expose email addresses via hidden fields, reply-to headers, or misconfigured plugins. Spam bots will scan the page source for anything that looks like an email address.
Prevent it:
- Disable comments entirely or auto-close after 14 days.
- Use a form tool that masks backend notifications (like Gravity Forms).
- Scan your page source (CTRL+U) and search for
@.
5. XML-RPC Fingerprinting and Attack Mapping
The xmlrpc.php file enables introspection. Attackers use it to probe login attempts, gather error messages, and identify plugins/themes based on their response behavior.
Prevent it:
add_filter('xmlrpc_enabled', '__return_false');Or use a Web Appliation Firewall (WAF) like Cloudflare to block access to /xmlrpc.php.
6. Password Reset Form as a Probe
Attackers use the password reset form to test if common email addresses exist. WordPress leaks validation feedback (“Check your email”) that confirms the account’s existence.
Prevent it:
- Use a plugin like WPS Hide Login.
- Obfuscate or customize error responses from the login system.
7. Leakage via Third-Party Plugins
Plugins may store or output emails in raw HTML, JavaScript variables, or shortcode output.
Prevent it:
- Audit your page source for
@symbols. - Use dev tools or CLI crawlers (e.g.
grep -r "@yourdomain.com"). - Vet plugins and only use ones that are actively maintained.
8. Reverse MX & WHOIS Enumeration
Hackers look up domains sharing your mail server (reverse MX) or find admin emails from WHOIS records. If you reuse the same admin email across services, it becomes traceable.
Prevent it:
- Enable WHOIS privacy.
- Use role-based or private emails (e.g.
[email protected]). - Never reuse your WP admin email on public profiles.
9. Newsletter Signup Hijacking
If your marketing tool exposes sender emails in headers (like From: [email protected]), bots and scrapers log it instantly.
Prevent it:
- Use separate emails for marketing (e.g.
hello@ornewsletter@). - Send from subdomains if possible.
- Route replies through helpdesk tools instead of personal inboxes.
Bonus: How to Monitor if You’re Already Exposed
- Check Public Breach Dumps: Use Have I Been Pwned.
- Scan Your Site Source: Look for
@symbols using tools like Screaming Frog or Sitebulb. - Monitor REST and XML-RPC traffic: Use Wordfence or Query Monitor.
- Set up email alerts for repeated API probing: Track access to endpoints like
/wp-json/wp/v2/users.
How We Prevent These Attacks with Static WordPress
Headless Hostman is a fully integrated Static Site Generator and hosting platform.
- Manage WordPress, like you always do
- When you want something to go live, push the page, do a partial push, or a full push
- The live site is fully Static
1. Static Websites Are More Secure, Period
All of the endpoints we mentioned above? They only exist on your WordPress staging website, which you use to push your pages and site Static. They are then fully relegated to managing your non-public website.
On the Static site, none of those links work. Instead, they just trigger 404 errors leaving hackers scratching their heads.
In addition, the live website is completely discombobulated from the database. It runs on a flattened, serverless environment.
2. Administrative Lockdown Tools
So, your Static site is decoupled from a database and all of those endpoints. Nice, what now?
You still have a WordPress site to control your content and deployments from. We take great measures to make sure the WordPress site address sending content to your Static live site is locked down.
But what if for some reason it does get discovered? Our admin lockdown tools play a vital role in adding extra measures of security.
We Offer the Ability to Lock It Down
By using our two-step verification process, you can totally lock down the wp-admin to anyone not authorized.
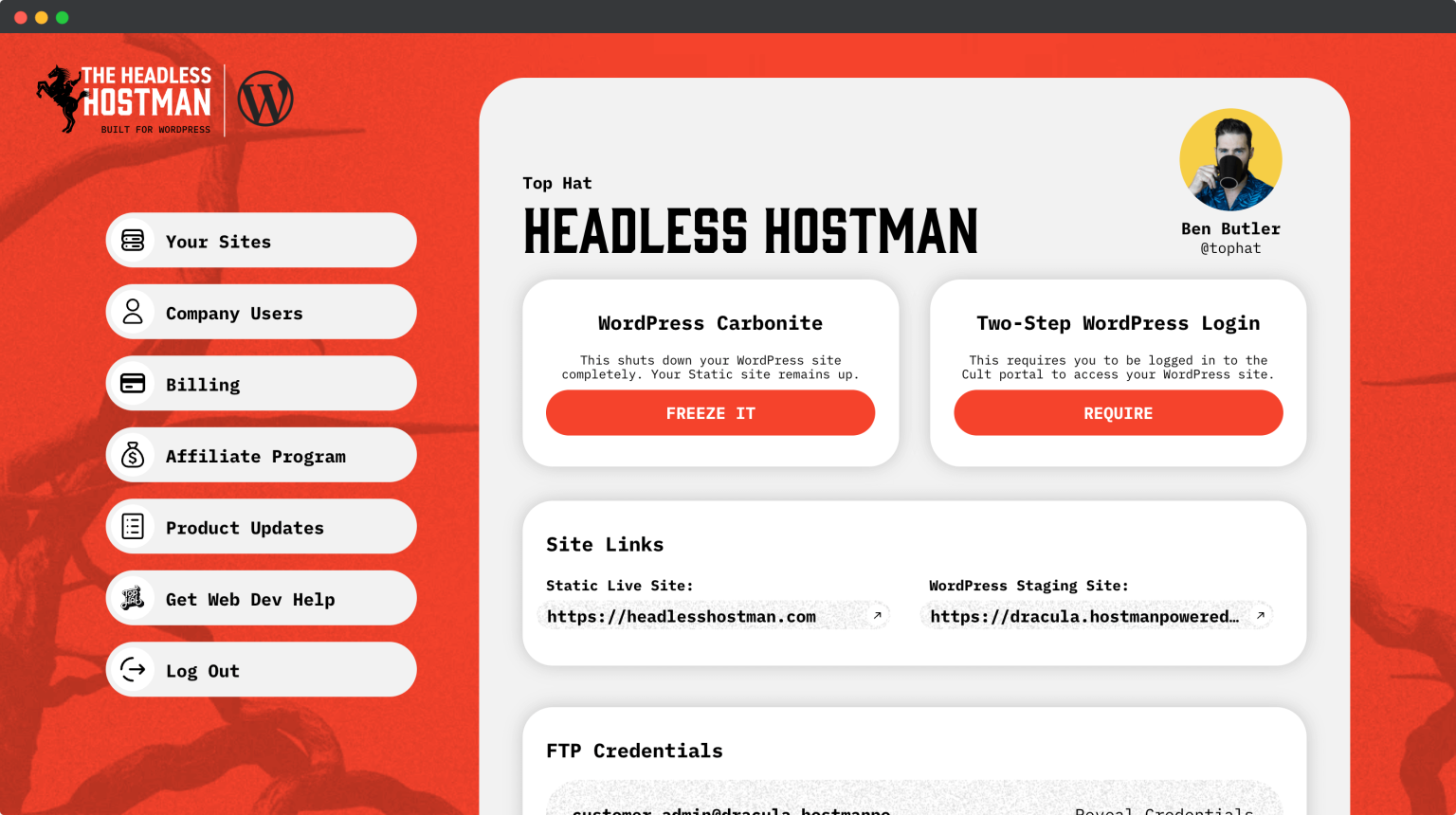
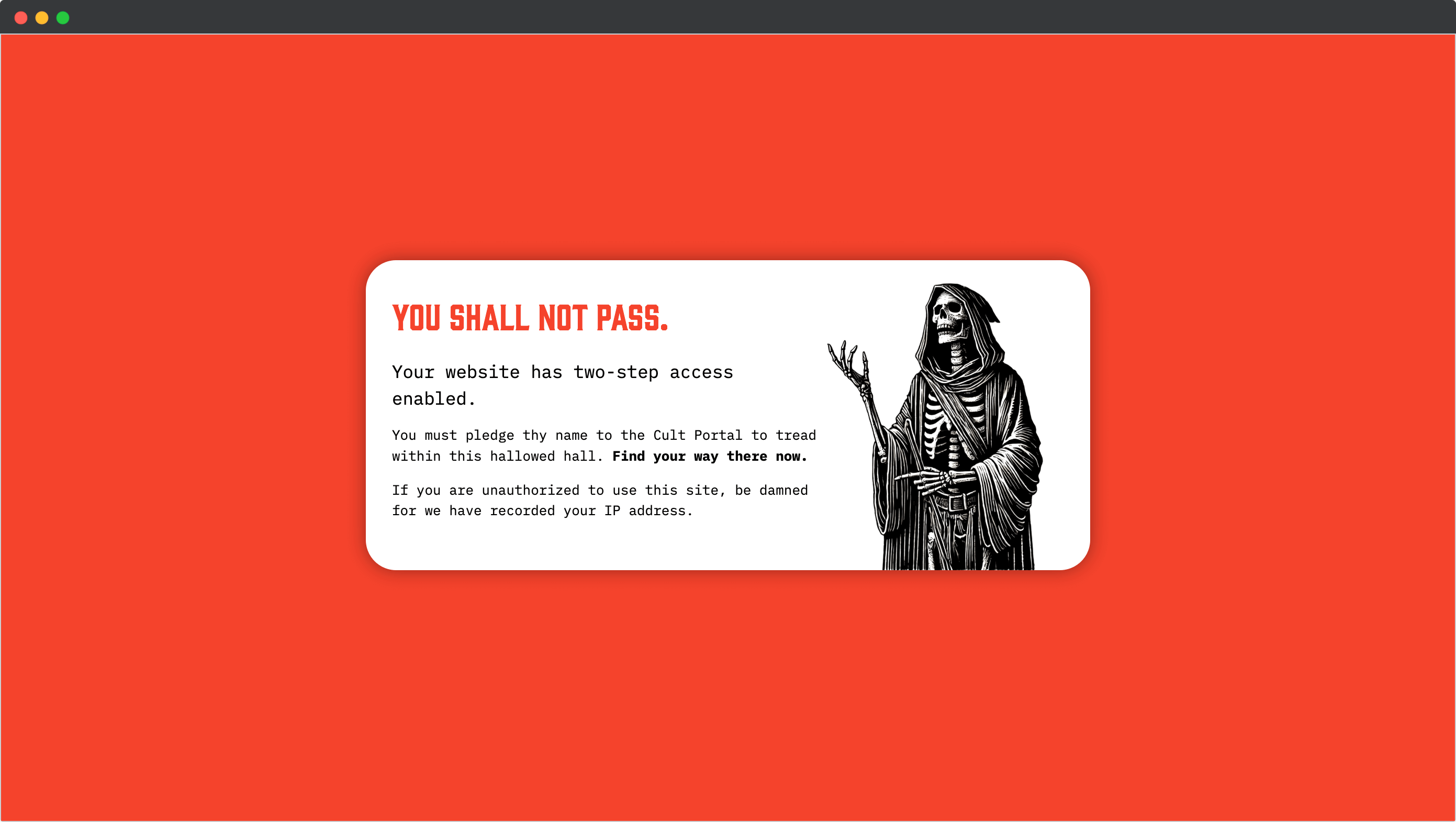
We do this by requiring login to our Cult (website management) portal, followed by a request to get access to the site.
Anyone who isn’t logged in through this method? They get this lovely red screen of death.
Or Just Disable It…
Secondarily, let’s say you don’t manage your site very often and don’t want to worry about it.
You can opt to just put it “On Carbonite.”
That feature shuts down the wp-admin and WordPress site completely until you’re ready to resume.
Concluding
Your admin email is a critical part of your WordPress security posture. It’s the thread that, when pulled, can unravel your login page, your inbox, your domain ownership—even your revenue stream.
Hackers aren’t always trying to brute force your password. Sometimes they’re just collecting data—quietly, automatically, and persistently—until one tiny detail cracks open everything.
The best defense? Think like an attacker. Then close every door you find.
If your platform or business relies on WordPress, consider hardening your surface with static generation, endpoint lockdowns, and obfuscation strategies that leave scrapers in the dark.
Deeper into the Abyss